1 Making Sense of Application Security
Modern software faces relentless and costly attacks, and vulnerabilities can surface at any layer—from CPUs to browsers to application code. Recent incidents show that breaches carry multimillion-dollar consequences and can threaten entire businesses, prompting organizations to elevate security leadership and accountability. The chapter’s central message is that security is a shared responsibility: everyone who builds and runs systems plays a role, with developers pivotal to preventing, detecting, and mitigating risk.
For developers, the expectations are clear: use product security features correctly, follow corporate standards, design with security in mind, and embrace DevSecOps practices. The chapter presents a layered view in which standards, protocols, and patterns underpin the libraries and frameworks developers use. Mastering fundamentals like TLS and OAuth/OpenID Connect makes tools such as Spring Security far easier to configure, reason about, and debug. By learning the underlying concepts, developers can communicate effectively with assessors and InfoSec, pass audits with fewer surprises, and build defenses that are robust by design.
The chapter also spotlights software supply chain risk: large dependency trees amplify exposure to known CVEs and malicious package changes. Teams must inventory all direct and transitive components, automate vulnerability scanning in CI/CD, rescan as advisories evolve, and use automated upgrades when tests permit—while writing against public APIs to keep upgrades feasible. Finally, it maps the broader security ecosystem—from mathematicians and cryptographers to standards authors, framework builders, InfoSec, auditors, and attackers—and narrows the developer’s mandate: apply proven standards, implement identity and authorization correctly, secure service-to-service communication, spot and fix common mistakes, and make pragmatic tradeoffs that keep software trustworthy.
Headlines showcasing major recent data breaches and security vulnerabilities, emphasizing the widespread impact on millions of users and the persistent threat to digital security.
Layers at the top depend on the layers below them. All the layers are required to produce secure application. The standards, protocols, and patterns used to secure applications are the primary focus of this book, they are the foundation that you need to use security libraries in your application effectively.
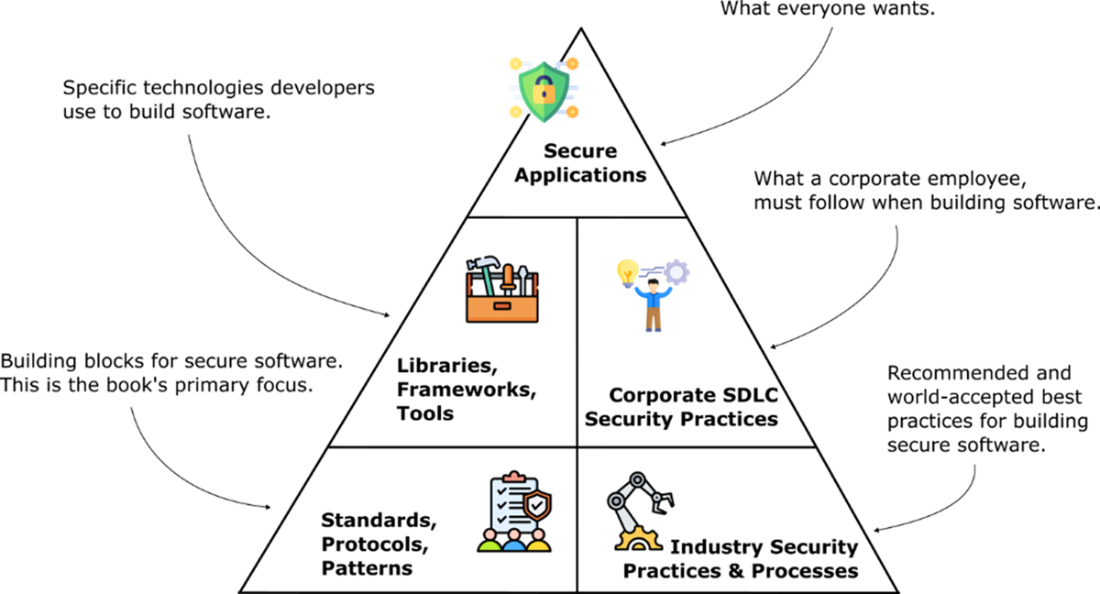
While developers often focus on libraries, frameworks, and tools at the mid-level, true security stems from foundational knowledge of standards, protocols, and patterns, as well as adherence to corporate and industry security practices. Bridging the gap between these layers leads to more effective and secure development.
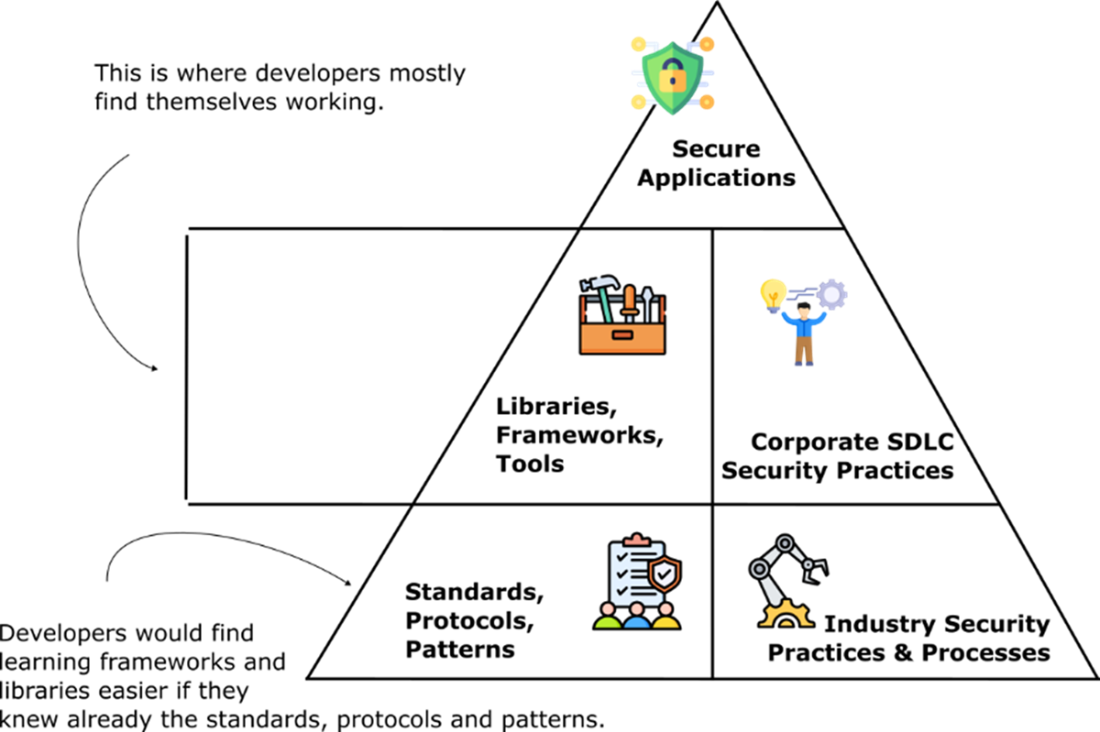
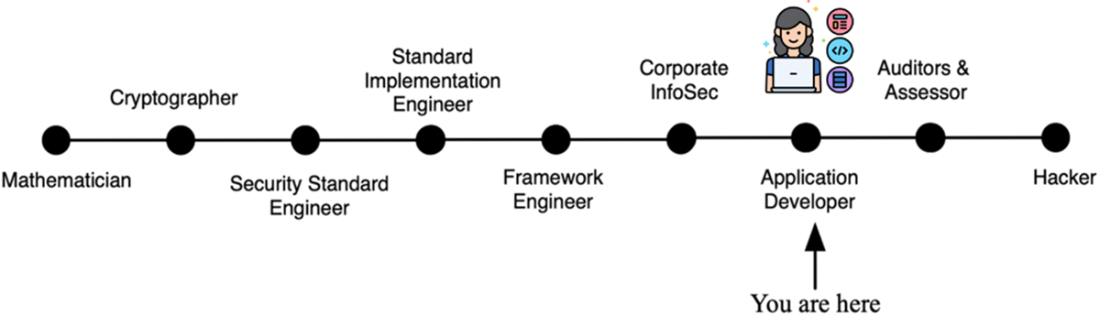
The spectrum of technical roles involved in computer security roles and responsibilities
Summary
- Security vulnerabilities can exist at every layer of the stack, from hardware (e.g., Meltdown, Specter) to application code.
- Security is everyone’s responsibility, not just InfoSec teams - developers play a central role.
- The business impact of breaches is massive (e.g., Marriott, Equifax), often costing millions or even billions.
- CISOs expect developers to:
- Use all product security features
- Follow corporate security standards
- Design and implement secure applications
- Embrace DevSecOps practices
- Security libraries (like Spring Security) are essential but hard to use unless you understand the underlying standards and protocols.
- Supply chain attacks (e.g., Equifax Apache Struts, Event-Stream Bitcoin theft) highlight the need for vigilance in managing dependencies.
- Automated vulnerability scanning in CI/CD pipelines is a best practice to detect and fix issues quickly.
- Stick to published APIs in libraries to ensure maintainability and security over time.
- Different roles contribute to security: mathematicians, cryptographers, standards engineers, framework engineers, InfoSec teams, auditors, and developers.
- Developers don’t need deep expertise in all these roles, but they must understand enough to apply standards and use libraries correctly.
- This book teaches developers the foundations (cryptography, protocols, standards) so they can confidently build secure, reliable applications.
 Software Security for Developers ebook for free
Software Security for Developers ebook for free