1 Introduction to Wasm on the server
WebAssembly (Wasm) is a portable, binary instruction format that acts like a hardware-agnostic target for compiled code, originally created to bring near-native performance to the browser. With the WebAssembly System Interface (WASI), those same qualities extend beyond the web: a host runtime provides controlled access to operating system capabilities, allowing Wasm modules to run on servers. In today’s landscape of microservices, containers, serverless, and edge computing, this makes Wasm a compelling foundation, particularly where portability, consistency, and operational simplicity are critical.
On the server, Wasm’s strengths cluster around performance, security, and flexibility. It is language-agnostic, lightweight to run, and hardware-independent, enabling “compile once, run anywhere” across diverse environments (from x86_64 to ARM). Its capability-based sandbox delivers strong isolation by default, reducing blast radius in modern, componentized systems. In practice, Wasm achieves near-native speeds for many compute tasks, while its very small artifacts and fast cold starts translate into higher workload density, lower costs, and improved responsiveness—benefits that shine in PaaS, FaaS, Kubernetes, and at the edge. Crucially, Wasm and WASI are open, standards-based, and vendor-neutral, helping teams avoid lock-in while integrating with familiar container tooling and image formats.
Wasm is best suited to serverless and edge workloads that value quick startup, minimal footprint, and safe extensibility, and it also excels for plugins, polyglot systems, cross‑platform apps, and even microcontroller scenarios. Current challenges include limited multi-threading (affecting highly concurrent, latency-sensitive services), uneven language ecosystem maturity, and less integrated debugging across some toolchains. Proposals like threads and garbage collection are closing these gaps, and many platforms mitigate concurrency needs via instance-per-request models. In short, reach for Wasm when portability, isolation, and startup speed matter most; prefer traditional containers or native runtimes where mature multithreading and established language ecosystems are the priority.
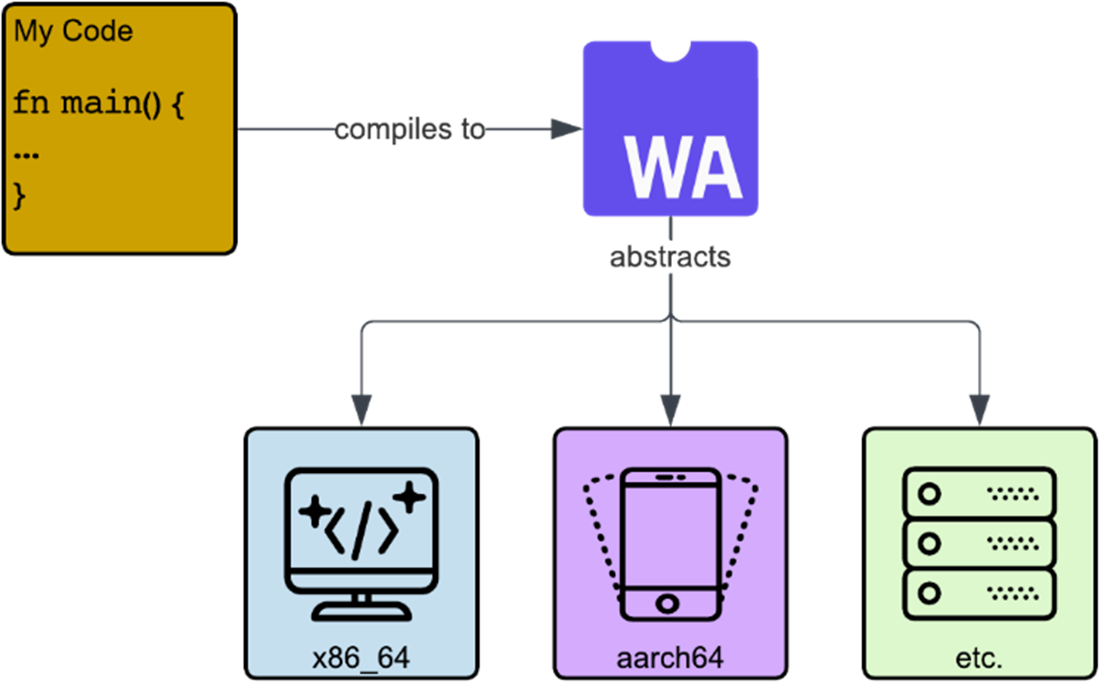
Wasm as an abstraction layer virtualizing over various kinds of hardware.
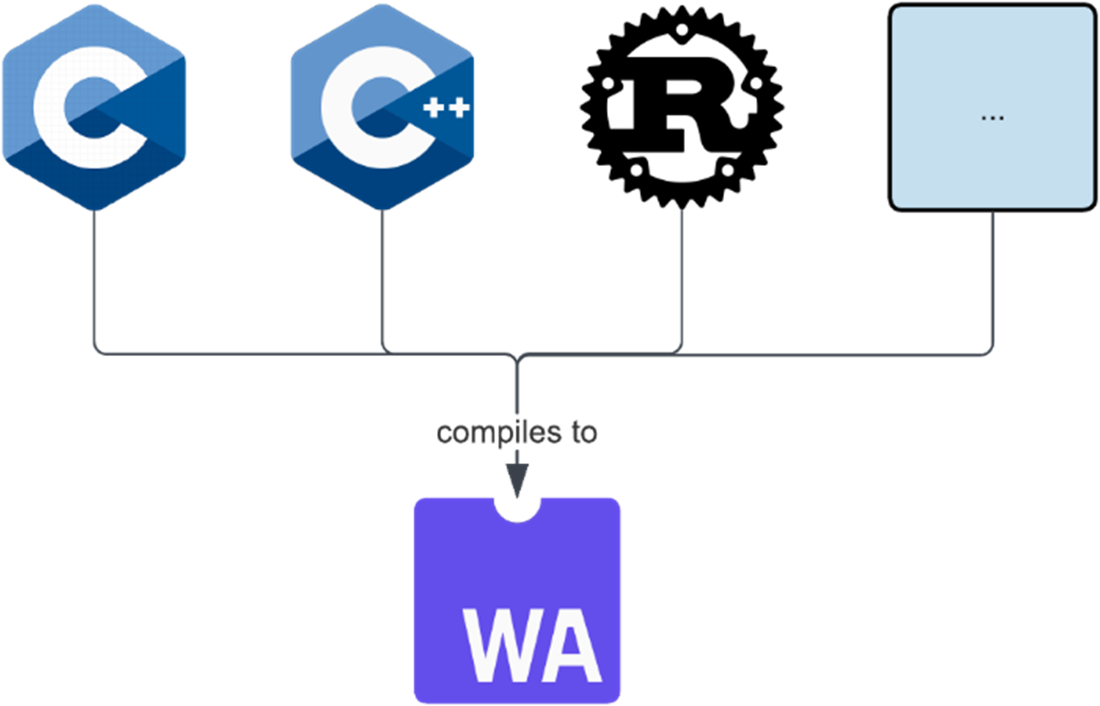
Compiling to Wasm from various languages.
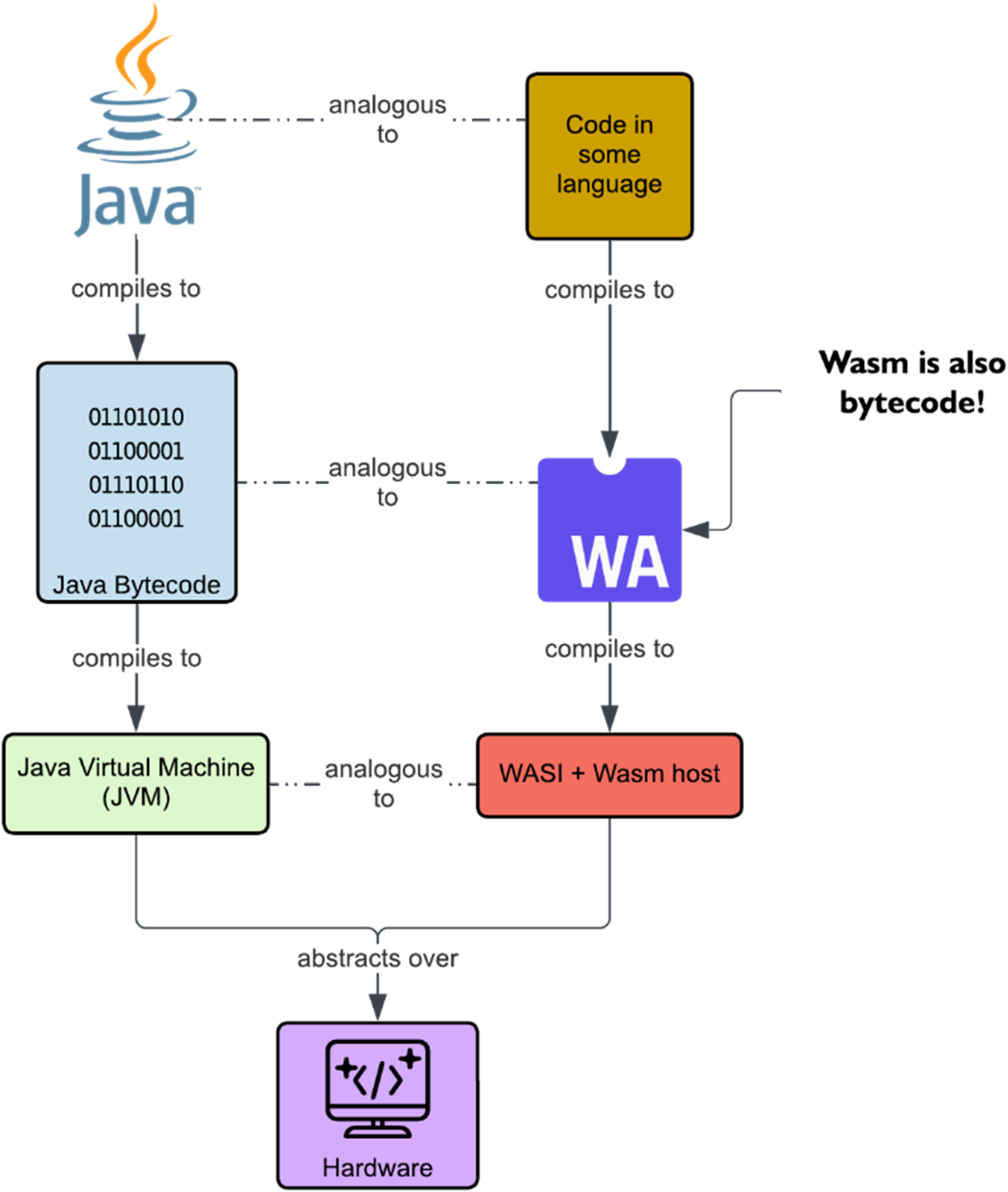
Java and Wasm's similarities
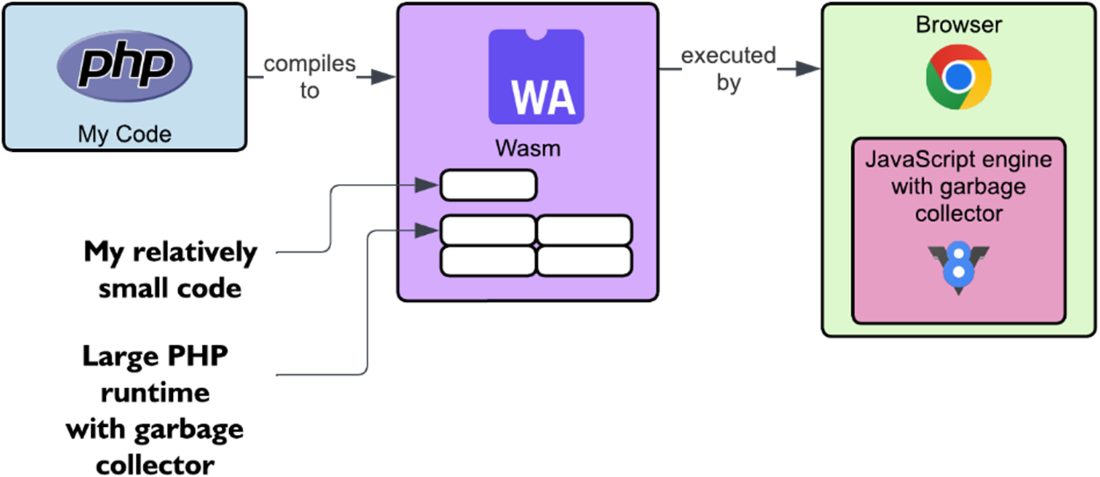
Running a PHP Wasm without garbage collection application in the browser.
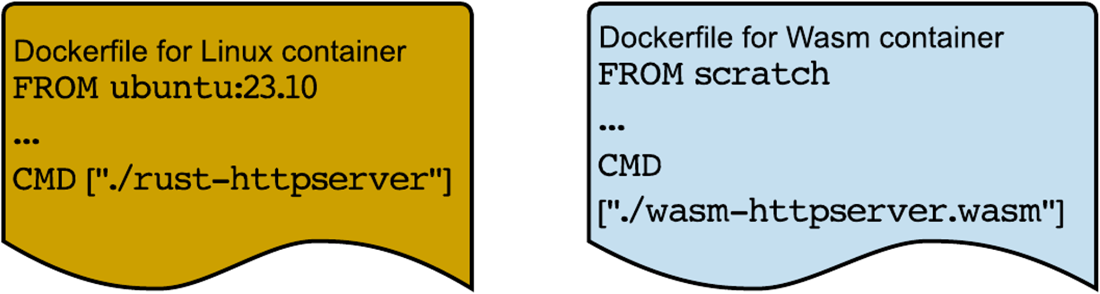
Dockerfiles for a Docker container and a Wasm container
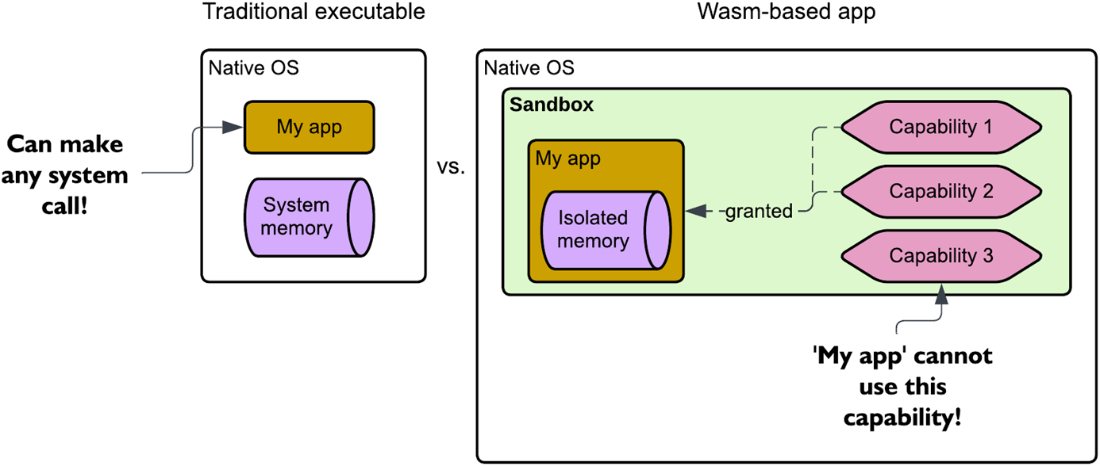
A native (traditional) application security model vs. Wasm's capability-based security model.
Summary
- Wasm is akin to an ISA like x86_64, in the sense that your code can target it for compilation. But it is not a real platform, and instead, just virtualizes actual hardware.
- Wasm apps can run outside of browser primarily through the Wasm System Interface (WASI) that allows communication with the OS.
- Docker supports running two types of containers: the traditional Docker container, and the newly introduced Wasm container.
- Wasm's language-agnosticism makes it so that over 40 languages can be compiled to it, but that is a double-edged sword as support for a particular language might not be as mature as it is for others.
- While benchmarks show that standalone Wasm apps can be 10-50% faster than containerized apps, real-world applications can struggle due to Wasm's lack of support for multi-threading.
- Wasm, when paired with serverless and its scale-to-zero requirement, leads to 80% faster execution times on average when compared to traditional serverless technologies.
- A Wasm binary is completely independent of the platform or hardware where it is built and can theoretically run on any system due to its hardware-agnosticism property.
- Wasm employs a capability-based security model that restricts the binary to only access the native OS through specific capabilities made available by the Wasm runtime.
- Aside from serverless and edge computing, Wasm has found its footing in mobile and desktop applications, microcontrollers, smart contracts, and polyglot programming.
- When targeting Wasm, it is commonplace to make sacrifices of particular packages that do not support Wasm.
 Server-Side WebAssembly ebook for free
Server-Side WebAssembly ebook for free