This chapter argues that teams can achieve stronger, more sustainable security by centering their work on good design rather than treating security as a separate checklist or a set of bolt-on features. In typical projects, security work drifts down the backlog, developers feel ill-equipped to be security experts, and last-minute audits or incidents expose costly gaps. Reframing security as a cross-cutting concern—and embedding it into everyday design decisions—creates systems that better withstand real-world threats without constant, explicit “think security” effort.
The authors define design as every deliberate decision from code-level choices to architectural structure, then show why the traditional approach falls short: it competes with business priorities, assumes universal security expertise, and can only guard against known vulnerabilities. Instead, focusing on domain precision naturally reduces risk. Treat security as concerns like confidentiality, integrity, availability, and traceability (CIA-T), and model the domain with exact types and invariants. For example, representing a username as a dedicated value object with strict rules both reflects true business meaning and blocks classes of attacks (such as XSS) by construction. This design-centric mindset aligns business and security priorities, enables non-experts to write safer code, and solves many “security bugs” as ordinary correctness issues.
The chapter also illustrates practical design tactics for input handling and parsing. Favor precise domain types over generic strings and validate in the right order (length, lexical content, then syntax). In a deeper example, it tackles XML entity expansion (the Billion Laughs attack) with layered defenses: configure parsers to constrain dangerous features, run a fast lexical scan to reject inputs lacking required elements or containing entities, and apply operational limits to isolate and cap resource usage. Combined, these measures provide defense in depth. The guidance concludes by encouraging an eclectic stance: keep the design focus while complementing it with traditional practices (such as penetration testing and secure output encoding) to achieve robust, secure-by-design software.
Figure 1.1. Having only a login page doesn’t help much.
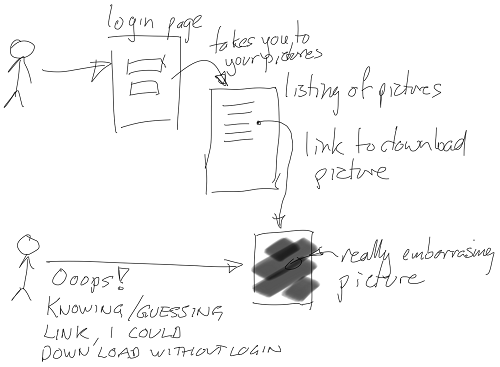
Figure 1.2. Traditionally, software security is viewed as explicit activities and concepts.

Figure 1.3. A focus on design rather than on security avoids issues with the traditional approach to security.
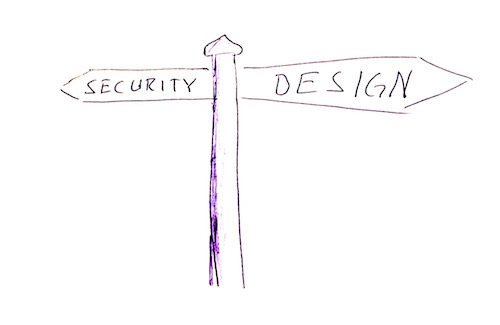
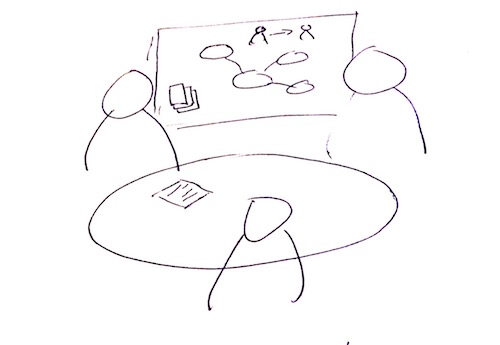
Figure 1.4. Exploring concepts with domain experts to gain deeper insight into the domain
Summary
- It’s better to view security as a concern to be met than to view it as a set of features to implement.
- It’s impractical to achieve security by keeping it at the top of your mind all the time while developing. A better way is to find design practices that guide you to more secure solutions.
- Any activity involving active decision making should be considered part of the software design process and can thus be referred to as design.
- Design is the guiding principle for how a system is built and is applicable on all levels, from code to architecture.
- The traditional approach to software security struggles because it relies on the developer to explicitly think about security vulnerabilities while at the same time trying to focus on implementing business functionality. It requires every developer to be a security expert and assumes that the person writing the code can think of every potential vulnerability that can occur now or in the future.
- By shifting the focus to design, you’re able to achieve a high degree of software security without the need to constantly and explicitly think about security.
- A strong design focus lets you create code that’s more secure compared to the traditional approach to software security.
- Every XML parser is implicitly vulnerable to entity attacks because entities are part of the XML language.
- Using generic types to represent specific data is a potential door opener for security weaknesses.
- Choosing XML parser configuration is difficult without understanding the underlying parser implementation.
- Secure by design promotes security in-depth by adding several layers of security.
 Secure by Design ebook for free
Secure by Design ebook for free