1 Introduction to cybersecurity metrics
This chapter introduces cybersecurity metrics as the essential refinery that turns abundant, raw organizational data into decision-ready intelligence. It argues that metrics illuminate risk, performance, and alignment with business objectives, helping teams benchmark maturity, prioritize remediation, and communicate clearly with stakeholders. A cautionary lens—illustrated by well-known breach examples—shows how gaps in measurement can mask critical exposures, while effective metrics programs drive continuous improvement, resilience, and strategic security outcomes.
The chapter defines what makes metrics effective—actionable, relevant, and reliable—and explains how clear goals anchor measurement to strategy. It categorizes metrics by nature and intent (quantitative and qualitative; leading and lagging) and by derivation (possible, direct, derived, and indirect), showing how each supports assessment, prioritization, and ROI analysis. It warns against “metrics-driven” behavior that games numbers rather than fixes root causes. Traditional, reactive measures (such as incident counts and response times) remain necessary, but the chapter advocates complementing them with innovative, proactive metrics powered by predictive analytics, threat intelligence, and behavioral signals—paired with preventive policies—to better anticipate and mitigate risk.
Against a rapidly evolving threat landscape—AI-augmented social engineering, supply chain compromise, ransomware, and state-sponsored operations—the chapter emphasizes adaptive measurement and modern tooling, including a shift from SIEM-centric monitoring toward orchestrated, automated SOAR workflows. It positions frameworks as scaffolds for consistent practice and market credibility, highlighting NIST CSF v2.0, ISO/IEC 27001, CIS Controls, and HITRUST, while reinforcing that compliance does not equal security. Finally, it outlines how AI enables predictive metrics when fueled by high-quality data and rigorous validation, and stresses human oversight to counter bias and false positives. The book will use NIST CSF v2.0 as a practical backbone for selecting, building, and evolving metrics—showing how to integrate AI to move from reactive defense to proactive, measurable cyber resilience.
A comparison of the main functionality of SIEM vs SOAR

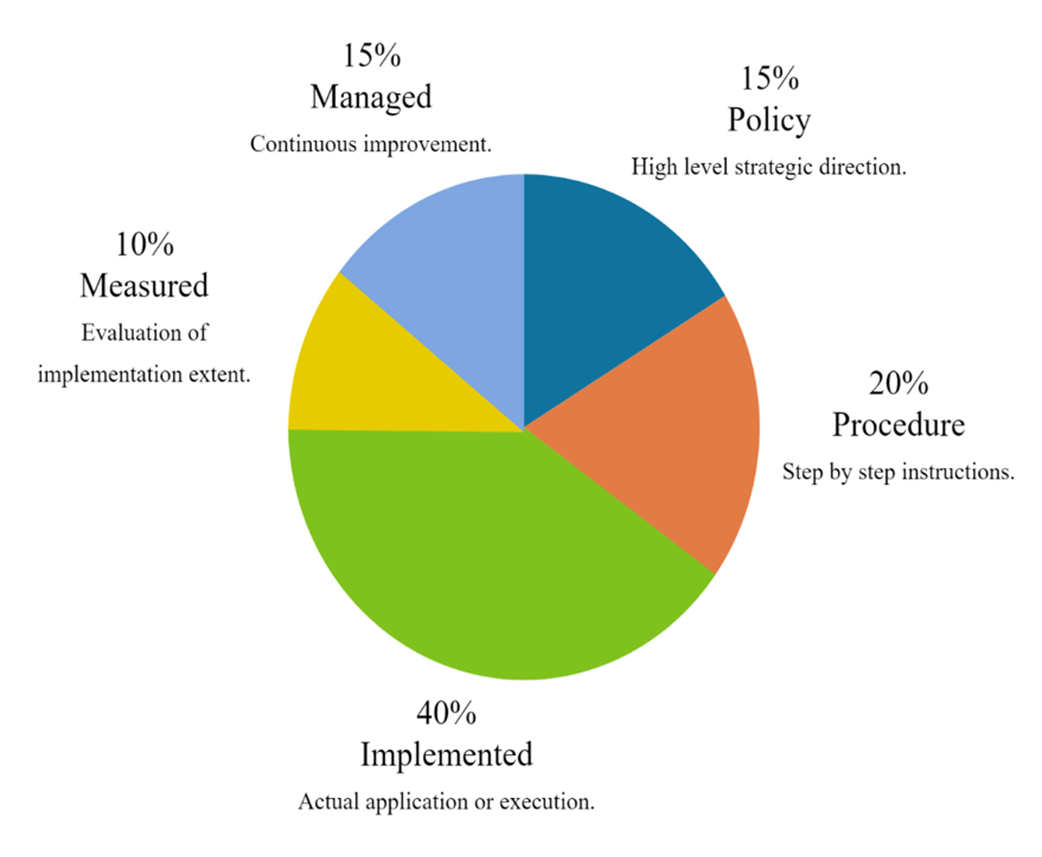
HITRUST scoring criterion by percentage. The percentages indicate the weights placed on each category for scoring purposes.
Summary
- Cybersecurity metrics quantify the effectiveness of cybersecurity programs and guide informed decisions by highlighting strengths and weaknesses.
- Frameworks like NIST CSF emphasize the importance of metrics in aligning security practices with industry standards and best practices.
- Traditional metrics measure the effectiveness of controls, helping to understand and improve the current security posture.
- Innovative metrics provide proactive measurements to anticipate and mitigate potential threats, enhancing security management efficiency.
- The dynamic cybersecurity threat landscape necessitates continuous monitoring and proactive measurement strategies to stay ahead of adversaries.
- AI enhances the predictive capabilities of cybersecurity metrics, enabling more efficient resource allocation and faster response times.
FAQ
What are cybersecurity metrics and why are they important?
Cybersecurity metrics are quantifiable measures that turn raw security data into actionable insight. They help organizations assess risk, track performance, and align day-to-day security activities with business objectives. By making trends visible and comparable over time, metrics enable better decisions, faster response, and stronger resilience against evolving threats.
What makes a cybersecurity metric effective?
Good metrics are:
- Actionable: they inform a decision or trigger a change.
- Relevant: they align to organizational goals and risk priorities.
- Reliable: they are accurate, consistent, and repeatable.
Set clear, measurable targets first—then use metrics to monitor progress and guide improvements.
What are the main types of cybersecurity metrics and when should I use them?
- Quantitative: numeric measures (e.g., incidents detected, mean time to respond) for trend tracking and benchmarking.
- Qualitative: context and judgments (e.g., training effectiveness, cultural impact) to explain the “why” behind numbers.
- Leading indicators: forward-looking signals (e.g., phishing attempt volume) to anticipate risk.
- Lagging indicators: outcomes (e.g., incident count, outage minutes) to assess past performance.
How do possible, direct, derived, and indirect metrics differ?
- Possible: trackable but not standard; collect only if value justifies effort.
- Direct: measured as-is (e.g., count of identity-related incidents).
- Derived: computed from other data (e.g., ratio of successful to failed logins).
- Indirect: come from adjacent business measures that illuminate security (e.g., incident reduction after training).
How do metrics help with benchmarking, prioritization, and communication?
- Benchmark and measure: assess cyber maturity and set realistic targets over time.
- Prioritize actions: focus resources where risk and impact are highest (e.g., unpatched high-severity vulns).
- Communicate and visualize: present clear trends (e.g., patch compliance, response times) to secure stakeholder buy-in.
What did the Equifax breach reveal about the importance of metrics?
The 2017 Equifax breach exploited an unpatched Apache Struts vulnerability. Metrics such as patch-policy compliance, time-to-remediate by severity, and coverage of high-risk systems could have exposed the gap earlier and prioritized remediation. The lesson: without visibility and prioritization metrics, critical vulnerabilities can remain unnoticed.
What’s the difference between traditional and innovative security metrics?
Traditional metrics (e.g., time to detect/respond, incident counts) are clear and useful but often reactive. Innovative metrics leverage predictive analytics, threat intelligence, and behavioral analytics to surface early signs of trouble (e.g., anomalous user behavior). Paired with proactive policies and controls, they enable anticipation and prevention—not just after-the-fact measurement.
How do SIEM and SOAR differ, and which metrics matter for each?
- SIEM: aggregates/correlates logs; triage is largely manual. Track alert volume, coverage, mean time to triage, and false-positive rate.
- SOAR: orchestrates and automates response. Track playbook success rate, automatic containment time, human override rate, and reduction in MTTR.
Both benefit from measuring detection quality and response effectiveness.
How do frameworks like NIST CSF, ISO/IEC 27001, CIS Controls, and HITRUST support metrics?
Frameworks provide structure for what to measure and why. NIST CSF v2.0’s six functions (Govern, Identify, Protect, Detect, Respond, Recover) offer a lifecycle to align metrics. HITRUST’s prescriptive model emphasizes Policy, Procedure, Implemented, Measured, and Managed. CIS Controls prioritize actionable safeguards. Crosswalks let you map metrics across frameworks for compliance evidence and program improvement.
How is AI used in predictive cybersecurity metrics, and what pitfalls should we watch for?
AI and ML detect patterns and anomalies faster than humans, enabling predictive alerts and faster response. Measure precision/recall, false-positive rate, time to detect/respond, model drift, and coverage. Success depends on high-quality, de-biased data, rigorous validation, and human oversight. Watch for bias, alert fatigue, and overreliance on models; layer AI with traditional controls and processes.
 Data-Driven Cybersecurity ebook for free
Data-Driven Cybersecurity ebook for free