1 Why authorization matters: Securing access in a digital world
Modern digital systems depend on more than verifying who a user is—they must also control precisely what that user can do. This chapter illustrates the stakes with the 2013 Target breach, where weak authorization boundaries turned a contractor credential compromise into a major incident. It explains how digital identity underpins both security and product functionality: authentication recognizes entities, accounts remember them, and authorization governs their actions. Far beyond protecting IT, authorization enables core experiences in cloud apps and platforms—such as document sharing, multi-tenant isolation, and fine-grained controls at global scale.
Traditional, static approaches like ACLs and RBAC struggle with today’s scale and complexity. They are hard to maintain, inflexible to context (device, time, location, risk), inefficient across distributed systems, opaque to audit, and prone to over-permissioning—undermining both security and compliance. Dynamic authorization addresses these gaps by evaluating policies at runtime, enabling just-in-time and context-aware decisions. The chapter introduces policy-based access control (PBAC) and two complementary representations: Policy as Code (general, reusable, testable rules) and Policy as Data (relationship- and attribute-driven permissions). Used together, they deliver scalable, fine-grained, auditable, and consistent decisions required by zero trust, multi-tenancy, consent-based access, PAM, and complex domain rules.
Authorization has become a strategic business capability. Trends like SaaS, zero trust, IoT, evolving regulations, and AI agents demand flexible, fine-grained controls that are easy to change and prove. Dynamic authorization reduces operational costs (fewer manual changes and access tickets, safer onboarding/offboarding), improves agility (policy changes over code changes), enhances customer experience (secure sharing, tiered features, per-tenant rules), and strengthens security and compliance (least privilege, contextual access, comprehensive logging). Treating authorization as a core platform—rather than scattered logic in apps—turns a liability into a differentiator and equips organizations to scale securely and compete effectively.
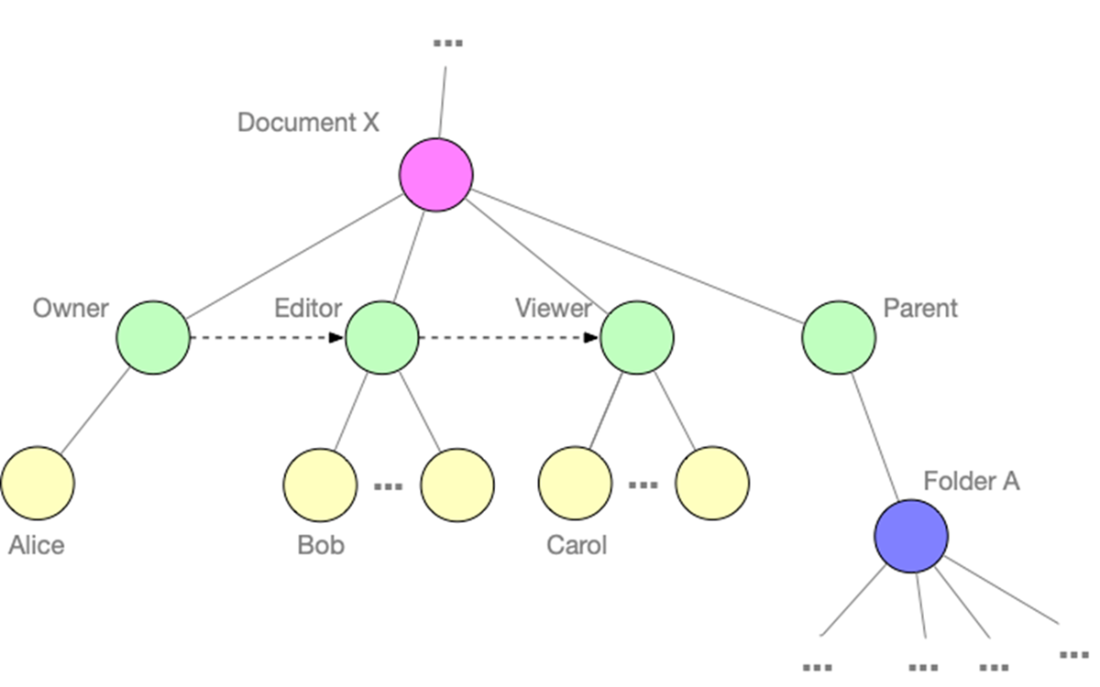
A relationship graph representing access to a Google document. Rather than use static ACLs, this model captures roles (like Owner, Editor, Viewer) as first-class relationships between users and resources. The graph also models hierarchical relationships (such as parent folders), enabling more flexible, general-purpose authorization logic that can be queried and evaluated dynamically.
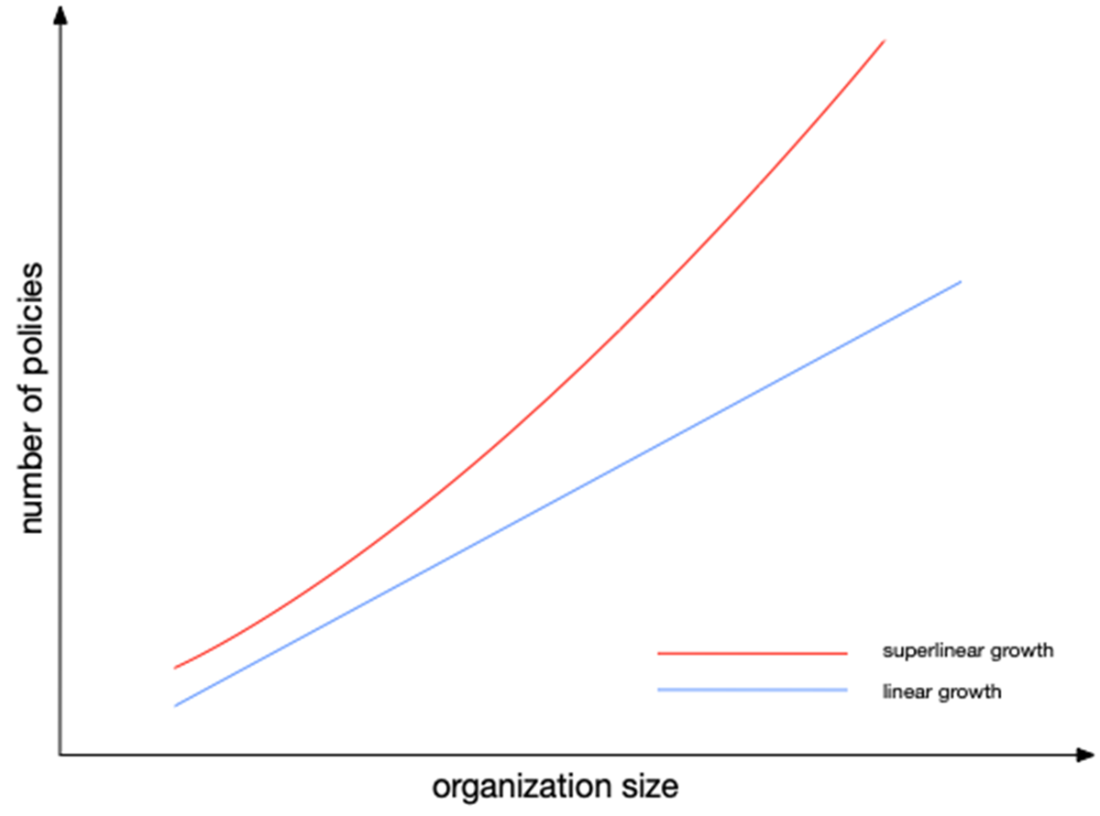
As an organization grows, the number of access policies tends to increase faster than linearly. Though a small organization might manage with a simple, flat set of policies, larger organizations face compounding complexity due to team structures, regional compliance, and overlapping responsibilities, leading to superlinear policy growth.
Summary
- Poor access control can lead to severe security breaches, as seen in the Target breach, where attackers exploited weak authorization to access sensitive systems.
- Authorization is not just about security; it also enables key features in modern cloud applications, such as document sharing and multi-tenant access control.
- Traditional authorization methods like ACLs and RBAC are static and struggle with scalability, flexibility, maintainability, efficiency, auditability, and security.
- Dynamic authorization overcomes these challenges by using policies to make real-time, context-aware access decisions.
- Policy-based access control (PBAC) enables fine-grained authorization by externalizing access control logic, making it dynamic and adaptable to changing conditions.
- The shift toward zero-trust security models, SaaS applications, IoT, regulatory compliance, and AI-driven applications demands more flexible and scalable access control, making dynamic authorization essential.
- Policies can be represented as code or data, enabling both structured rule enforcement and flexible, real-time access adjustments.
- Treating policy as code allows version control, testing, and automation, while policy as data supports fine-grained, user-defined access controls.
- Organizations adopting dynamic authorization benefit from reduced operational costs, improved agility, enhanced security, and better customer experiences.
- Businesses can use dynamic authorization as a competitive advantage, enabling new product capabilities, faster compliance adaptation, and stronger security.
- Authorization is a strategic investment, not just a security measure—organizations that adopt policy-based access control gain efficiency, scalability, and security.
 Dynamic Authorization ebook for free
Dynamic Authorization ebook for free