1 Security Concepts of Information Assurance
This chapter introduces the foundational concepts that underpin information assurance. It frames organizations as socio-technical systems in which people, processes, and technology work together to create value, and it defines assets broadly to include tangible items (facilities, hardware), intangible items (software, data, intellectual property, reputation), and human assets (employees, contractors, vendors). The goal of cybersecurity is to understand organizational risk, anticipate relevant threats, and select effective controls that preserve operations across increasingly hybrid and cloud-enabled environments.
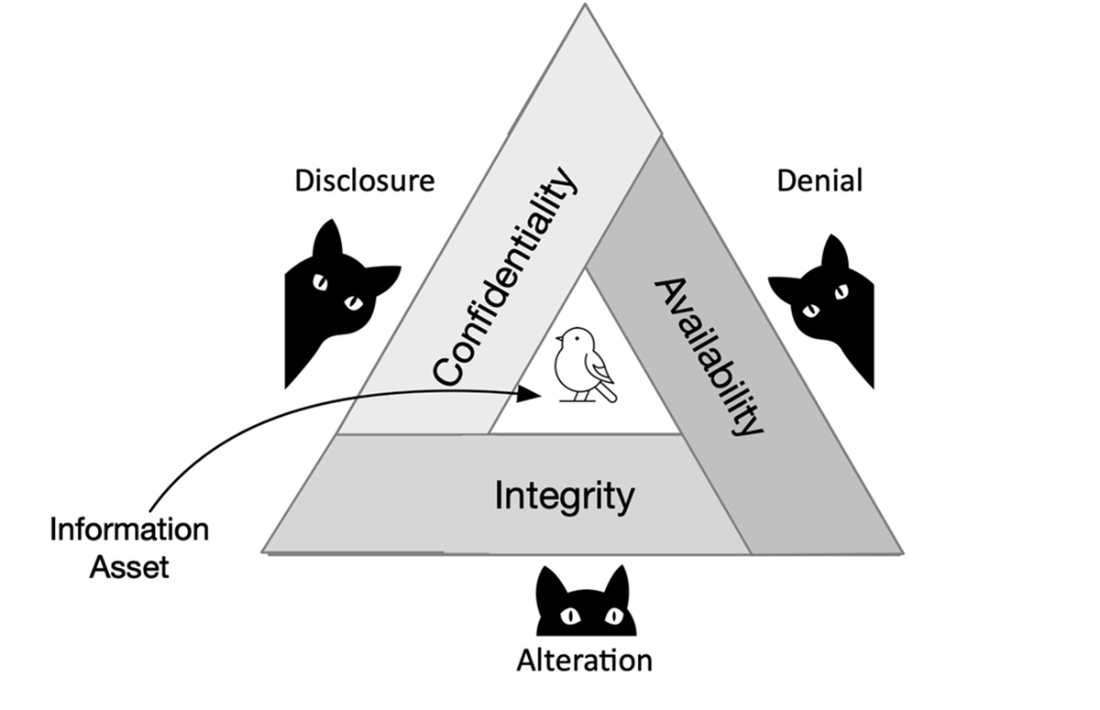
Key risk terms are clarified: vulnerabilities are weaknesses in assets, threats are factors that can exploit those weaknesses, attacks are intentional exploitations, and threat actors range from insiders and hobbyists to criminal groups and nation-state teams. Security controls are grouped as physical, technical, and administrative measures that collectively uphold the CIA triad—confidentiality, integrity, and availability—while countering the complementary threat classes of disclosure, alteration, and denial. Examples include encryption and access control for confidentiality, hashing and digital signatures for integrity, and redundancy, failover, and backups for availability; these controls often overlap and reinforce one another.
Because not all information carries equal risk, the chapter emphasizes data classification to align protections with sensitivity and impact—commonly using tiers such as public, internal, confidential, and highly confidential. It distinguishes sensitive from confidential data, explains how handling requirements become stricter as potential harm rises, and details categories like personally identifiable information (PII)—including both non-public and public elements that may enable identification—and protected health information (PHI), which demands strict privacy safeguards. Together, these concepts provide a practical framework for prioritizing defenses and applying the right controls to protect an organization’s most valuable assets.
Illustration of the interdependence of the key information security principles of confidentiality, integrity, and availability along with the corresponding threats of disclosure, alteration, and denial.
Answers to Review Questions
- The correct answer is D. Software is not a tangible asset. Unlike hardware, buildings, and machines, which have a physical form and can be touched, software is intangible. It consists of code and data that exist digitally rather than physically.
- The correct answer is C. Availability is the component of the CIA triad that focuses on ensuring that information is available when it is needed. On the other hand, while Confidentiality and Integrity are part of the CIA, they have different purposes. Authentication is not part of the CIA triad.
- The correct answer is A. Any factor that has the potential to disrupt an asset by exploiting a vulnerability is known as a threat. Threats can take many forms, including malicious actors such as hackers, computer viruses, or natural disasters such as hurricanes or earthquakes. The remaining options, on the other hand, are not threats because the first two unchecked options represent vulnerabilities, and the last unchecked option emphasizes the need for protective measures on an asset to counter potential threats.
- The correct answer is C. A threat actor is an individual or entity responsible for launching cyberattacks. The remaining options are incorrect because a software vulnerability is a vulnerability, a phishing email is a threat vector, and a denial-of-service attack is an example of an attack method.
- The correct answer is C. PII (Personally Identifiable Information) includes personal information such as names and addresses, while PHI (Protected Health Information) is a subset that focuses on health information, including medical records and treatment details. PII and PHI must be protected, but PHI has additional regulatory requirements.
 Become ISC2 Certified in Cybersecurity ebook for free
Become ISC2 Certified in Cybersecurity ebook for free